7 Types of Data Security
Introduction
In the dynamic landscape of Types of Data Security, staying ahead is not just a strategy; it’s a necessity. We, at Ayoshya Technology, present a comprehensive exploration of cutting-edge data security technologies that go beyond the conventional. Our focus is on getting you familiar with the top 7 types of data security.
A Comprehensive Guide to Oracle Security
Top 7 Types of Data Security Technology
1. Encryption Technology
Encryption stands as the sentinel of data protection. Our guide navigates through the intricacies of encryption algorithms, ensuring a robust shield against unauthorized access. The mermaid syntax diagram below illustrates the encryption process:
Here’s how encryption works:
- An algorithm culation changes over the first text, known as plaintext, into an elective structure known as ciphertext.
- Just approved individuals who have the key can unravel the code and access the first plaintext data.

Some encryption procedures include:
- Elliptic curve cryptography
- Symmetric key encryption
- Network-Bound Disk Encryption (NBDE)
Most present day encryption techniques, combined with great passwords, are impervious to beast force assaults. Be that as it may, quantum processing could be a danger to encryption security later on.
Some potential next big things in encryption technology include:
- Quantum Cryptography
- Homomorphic Encryption
- Biometric Encryption
- Wearable Two-Factor Authentication
- Peer-To-Peer Encryption
- Widespread End-To-End Encryption
- Search Engines With Free VPNs
- Honey Encryption
Security Risks of Increased Mobility With S/4 Hana
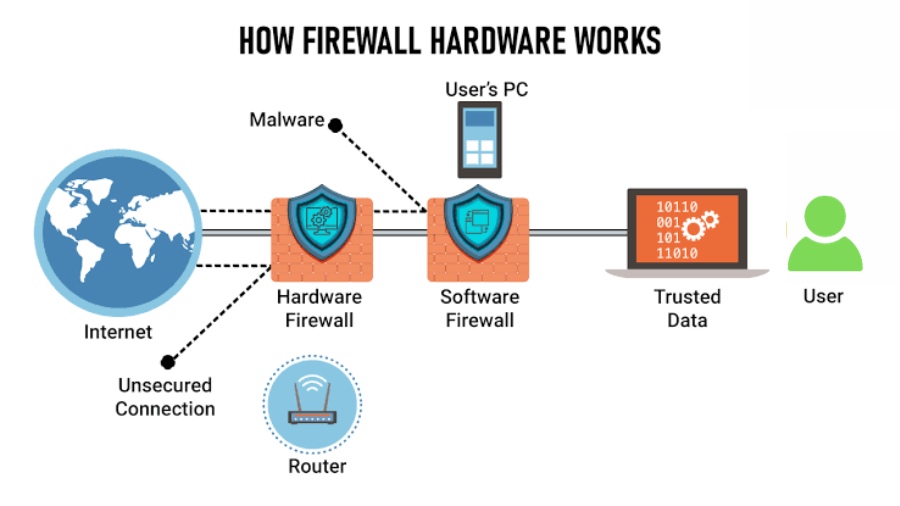
2. Firewall Solutions
Firewalls are the guardians at the gate. Our guide dissects advanced firewall solutions, providing insights into next-gen firewalls, intrusion detection systems, and network segmentation. Learn how to construct an impenetrable defense against cyber threats.
A firewall is a PC network security framework that confines web traffic in to, out of, or inside a confidential organization. This product or committed equipment programming unit capabilities by specifically obstructing or permitting information parcels
3. Intrusion Detection and Prevention Systems (IDPS)
The eyes and ears of your security infrastructure. We delve into the realm of IDPS, unraveling the intricacies of anomaly detection, signature-based detection, and real-time threat response. Stay ahead in the cat-and-mouse game of cyber threats.
IDPS can:
- Monitor network traffic
- Detect suspicious activity
- Alert users of suspicious activity
- Prevent intrusions by blocking or stopping activity
IDPS can detect signs of malicious activity, such as:
- Hacking attempts
- Malware infections
- Data breaches
- Unauthorized access
- Misuse
- Modification
- Denial of a computer or network
4. Secure Access Control Measures
Controlling access with precision. Our guide explores biometric authentication, multi-factor authentication, and role-based access control. Implement a robust access control strategy to ensure only authorized personnel have entry.

Here are some secure access control measures:
- Authentication: Ensures that only the right people are granted access
- Encryption: Makes data unreadable without the right decryption keys
- Security awareness training: Teaches staff about potential threats, best practices, and their role in security
- Access control policy: Provides clear direction for security guards and clients
- Network security: Prevents unauthorized users from accessing storage systems and data
- Email security: Protects email accounts and content from external threats
- Mandatory Access Control (MAC)
- Role-Based Access Control (RBAC)
- Discretionary Access Control (DAC)
- Rule-Based Access Control (RBAC or RB-RBAC)
5. Data Loss Prevention (DLP) Technologies
Preventing leaks before they happen. We provide an in-depth understanding of DLP technologies, from content discovery to policy enforcement. Safeguard your sensitive data with proactive measures.
DLP technologies utilize a mix of standard network protection gauges and high level arrangements. Standard measures incorporate
Firewalls
Endpoint protection tools
Monitoring services
Antivirus software
Advanced solutions include:
Artificial intelligence (AI)
Machine learning (ML)
Automation
Exploring Fiori OData Integration
6. Endpoint Security Solutions
Securing the last line of defense. Our guide covers endpoint protection platforms, antivirus solutions, and advanced endpoint detection. Ensure a comprehensive defense strategy from every device.

Features of endpoint security solutions:
- Centralized management
- Cloud integration
- Identity and access management (IAM)
- Automated threat detection and remediation
- User and entity behavior analytics (UEBA)
7. Security Information and Event Management (SIEM) Systems
The nerve center of cybersecurity. We unravel the functionalities of SIEM systems, from log collection to real-time analysis. Empower your security team with actionable insights for swift response.
SIEM technology gathers and examines security occasions and different information sources in close to ongoing and all things considered. It distinguishes movement that veers off from the standard and makes a proper move. SIEM arrangements permit associations to:
- Recreate past incidents
- Analyze new incidents
- Investigate suspicious activity
- Implement more effective security processes
- Respond to threats faster
Some things to consider when buying SIEM systems include:
- Personal data discovery
- Data inventory
- Privacy program automation
- Data processing inventory
- Data subject request
- Assessment automation
- Third party management
- Risk management
- Consent and preference management
Advancing Beyond Conventional Wisdom
Integrating Technologies for a Unified Defense
The future of data security lies in the integration of technologies. Our guide explores how combining encryption, firewall solutions, and SIEM systems forms a unified defense. Leverage the strength of each technology for a cohesive security strategy.
Conclusion
In conclusion, our guide transcends the existing narrative on data security technologies. It equips organizations with actionable insights, advanced strategies, and a holistic approach to safeguarding information. Stay ahead in the data security game—implement the best practices outlined in our comprehensive guide. Elevate your data security posture with precision and confidence.
Common FAQs
What is the main function of encryption technology?
- To protect data from unauthorized access.
What are some potential next big things in encryption technology?
- Quantum Cryptography, Homomorphic Encryption, Biometric Encryption, Wearable Two-Factor Authentication, Peer-To-Peer Encryption, Universal End-To-End Encryption, Search Engines With Free VPNs, Honey Encryption.
What is the purpose of a firewall?
- To restrict internet traffic to and from a private network.
What are some of the malicious activities that the IDPS can detect?
- Hacking attempts, malware infections, data breaches, unauthorized access.
What is the role of access control measures in data security?
- To ensure that only authorized personnel have entry to sensitive data.